
|
|
|
 |
|
|
Information Security Field Study
Many global 1000 companies have made substantial cybersecurity investments to ensure information and connectivity within their firms is relatively secure. Meanwhile, for many smaller firms, data and intellectual property storage and protection may not be as sophisticated. As large firms and smaller firms collaborate, this "cybersecurity gap" highlights a risk large firms face wihin their extended enterprise. This field study is supported by the Department of Homeland Security, through the Institute for Information Infrastructure Protection. |
|||
|
Field Study reports: Manufacturing Sector
Health Care Sector
Financial Sector
Video: Eric Johnson on security challenges Costs of Information Infrastructure Failures, presented at WEIS 2006 Extended Enterprise Security, CABIT 2005 Information Security in the Extended Enterprise, presented at WEIS 2005
|
|||||
Our research approach is to quantify the perception of current cybersecurity-related risks and business opportunities on both sides of a business relationship through a set of interviews. The results will illuminate:
- The level of risk to supply chains from cyberattacks as a result of tighter integration;
- Mechanisms for mitigating that risk; and
- Barriers to tighter integration across the extended enterprise.
Modeling How Firms Adopt Information Security Capabilities
By looking at the process used by organizations to adopt information security measures, we can begin to both characterize the information security approach of companies, and determine the complete set of possible drivers for information security adoption by organizations. We will interview CIOs, CSOs, and other decision-makers about how their organization makes and implements information security investment decisions, following a framework that we believe to be generic enough to encompass most information security decision processes.
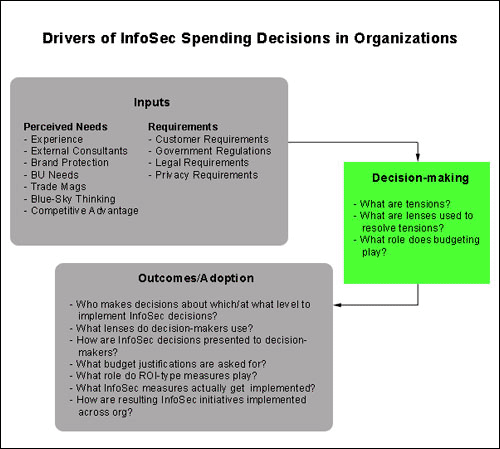
This framework will serve as the basis for discussions with decision-makers and influencers within the organization. There are three parts to this framework, shown in the figure above:
- "Inputs," that are used to inform the decision, both about possible risks, their consequences, and the business needs of the organization.
- "Decision-making factors," which include the processes by which tensions between competing priorities such as risks, budget and business needs are resolved.
- "Outcomes," which include the openness of the organization to adopt the recommendations of the information security officer, and what is actually implemented.
Are larger firms making better security investments (and better patch management decisions) than smaller firms, creating a security gap in the extended enterprise? How are firms managing risk across the extended enterprise? Should large, relatively secure firms be concerned about collaborating with smaller, less secure firms?
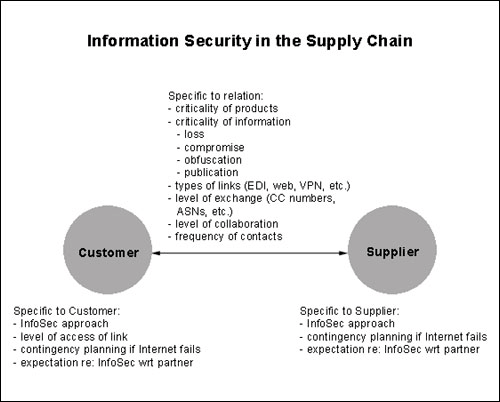
To address these issues we are studying the supply chain of the firms interviewed in the first focus above by interviewing some number of the customer's direct suppliers. Choosing firms of different sizes to study, we will be able to determine the relative information security stance of companies of various sizes, and thus whether a gap exists. By studying organizations and their supply chains, we have access to companies of a range of sizes. We are currently testing a metric that we will use to rank an organizations' information security stance. The metric encompasses the inputs to decision-making, the filters for resolving tensions, the level of adoption of security recommendations, and the actual information security measures implemented as measures of an organizational stance regarding information security.
Interdependency Risk Magnitude
If the security of a firm is increasingly dependent on the security at other firms in their extended enterprise, how large is the real or perceived security problem? What are the security risks and how do these translate into business risks? Knowing how vulnerable or resilient supply chains and extended enterprises are to security failures of one of their members will directly inform the policy debate about how much information security is needed for a public good.
![]()
| Return to the Center's Information Security Project | |
| Department of Homeland Security funds study - press release | |
| MBA Research Fellow Scott Dynes on "What Drives Information Security Investment?" Institute for Security Technology Studies | |
| "IT Security in the Extended Enterprise," M. Eric Johnson, Financial Times | |
| "Security Summit," Network World | |
| "Information Security and Privacy: At Odds with Speed and Collaboration?" - a Thought Leadership Summit on Digital Strategies | |
| "Security and Privacy: Business Dilemma or Opportunity?" - a Tuck alumni panel hosted by the Center for Digital Strategies | |
|
|